Background
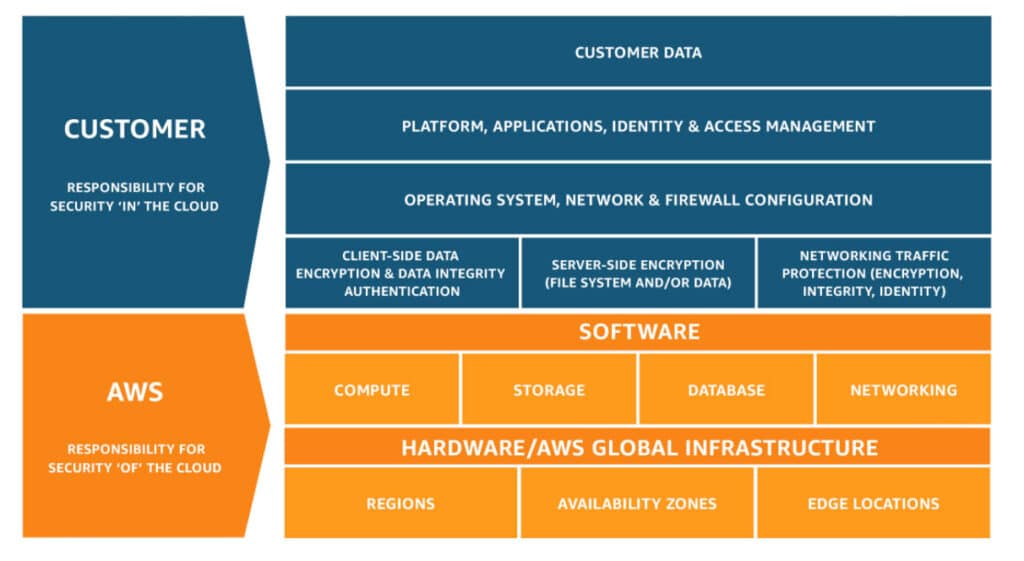
Amazon Web Services (AWS) held a security-oriented re:Inforce event on June 13th and 14th at the Anaheim Convention Center in California. The conference had over 5,000 attendees with a packed show floor mainly consisting of AWS Independent Software Vendors (ISVs), Global Systems Integrators (GSIs), and MSSP (Managed Security Service Partners (MSSPs). At the keynote, CJ Moses, CISO and VP of Security Engineering at AWS articulated how security is central in everything done at AWS and new security announcements to bolster AWS’s position as a leader in cloud security. Security responsibilities were delineated between AWS and customers, with AWS being responsible for the security “of” the cloud while customers are accountable for the security “in” the cloud. (See Figure 1 below).
Several announcements were made in cloud security, management tools, encryption, identity, and partner news and products. This blog post will cover a segment of these announcements related to security services that accelerate the application development lifecycle and other notable takeaways from the conference.
Announcements accelerating developer productivity:
Code Scans for Lambda in Amazon Inspector: Amazon Inspector, initially launched in 2015, is an automated vulnerability management service that continually scans AWS workloads for software vulnerabilities and unintended network exposure. Some features include continual, automated assessment scans, automatic discovery of EC2 instances and ECR repositories, and support for container-based workloads while streamlining security management and response across AWS services in the AWS Organization. The new feature of Amazon Inspector, Code Scans for AWS Lambda function, extends its scanning capability to custom proprietary application code within a Lambda function to detect code security vulnerabilities such as injection flaws, data leaks, weak cryptography, or missing encryption based on AWS security best practices.
Amazon CodeGuru Security: This service is a static application security testing (SAST) tool that uses Machine Learning to identify and guide users on code vulnerabilities. The capability provides in-context code patches for some vulnerabilities, lessening the developer’s effort to address these weaknesses. Leveraging deep semantic analysis of application code, CodeGuru Security can detect vulnerabilities with a low false positive rate and, with an API-based design, can be plugged in at any stage of the development lifecycle. Other than efficiencies gained by automation of fixing vulnerabilities, this capability can also be educational for developers learning how to avoid common security issues.
Amazon Verified Permissions: This service is a fine-grained authorization service for the applications you build and centralizes policies into a store, allowing developers to use these permissions to grant authorization for user actions. Developers can align their application access with Zero Trust principles by implementing least privilege and continual verification within applications. Security and audit teams can better analyze and audit who accessed what within applications. The permissions use Cedar, an open-source policy language, to define permissions. AWS open-sourced Cedar in May of 2023. The standard definition of fine-grained permissions reduces the complexity for developers across any application.
A note on AWS security partners
The re:Inforce conference had various sponsors present at the exhibit area, all focused on security. Customers are committed to cloud adoption but often prefer a third-party vendor to handle security. The ISV, GSI, and MSSPs collaborate with AWS to deliver top-level security to AWS customers. Although some overlap exists between partners and AWS services, the AWS Global Partner Security Initiative helps leverage the customer opportunity to benefit all parties. There were several announcements at the event that can be summarized as follows:
1. In partnership with AWS, Deloitte announced ConvergeSECURITY, an AI-enhanced and cloud-focused service offering enterprises secure cloud migration, compliance, threat detection, and resilience to expedite cloud transformation amid rising cyber threats. This helps enterprises address the global cyber talent shortage.
2. IBM Security is expanding its integrations with Amazon Web Services (AWS) to bolster cloud security, providing easier deployment through an AWS built-in solution, support for Amazon Security Lake via IBM’s QRadar Suite, improved data security features including new Guardium Insights SaaS editions and the integration of Polar Security’s Data Security Posture Management, and support for the AWS Global Partner Security Initiative to deliver security and compliance services.
3. Lacework, a data-driven cloud security company, is deepening its relationship with Amazon Web Services (AWS) to offer enhanced anomaly detection through composite alerts in collaboration with Amazon GuardDuty, as well as introducing an AWS integrated solution, all aiming to streamline security services and reduce investigation times for enterprises.
Customers prefer solutions that are easy to implement. AWS Marketplace now has a category of partner solutions with AWS built-in that install, configure, and integrate with key foundational AWS services such as AWS CloudTrail, AWS Security Hub, AWS Organization, and Amazon GuardDuty in an automated deployment package validated by AWS experts. This reduces the risk and accelerates the implementation cycle for customers.
AWS Cyber Insurance Partners have streamlined the process for AWS customers to get a quote for the cyber insurance coverage they need within two business days. With a simplified method of sharing AWS security posture using AWS Security Hub data, AWS Cyber Insurance Partners can offer valuable insights on how the customer can level up their security posture, thereby reducing the customer’s business risk while unlocking higher coverage limits or reducing cost on premiums.
AWS Security Strategy
AWS puts security as the top priority in delivering the message to customers that cloud workloads will be as safe or safer than on-premise workloads. Some highlights of how AWS provides infrastructure security and enables customer workload security on the security paradigm are listed below.
Silicon and Security at AWS: Last year, I wrote a detailed blog post on Amazon’s Silicon Investment highlighting AWS Inferentia, AWS Graviton, and the security-focused AWS Nitro System. The AWS Nitro System is the foundational technology to secure the latest generation of Amazon EC2 instances, designed to enhance efficiency and cost-effectiveness. By offloading virtualization tasks to dedicated hardware and software, Nitro System significantly reduces the attack surface, improving security through continuous monitoring and protection. This security model eliminates administrative access and potential human error. The Nitro System boosts performance and cost savings by allowing server resources to be used by instances. It accelerates I/O functions via dedicated Nitro Cards, thus delivering security-rich, high-performance cloud workloads.
Software and Security at AWS: AWS also took steps to secure workloads by innovating on the software layer with Firecracker, the open-source virtual machine monitor (VMM). Firecracker boosts security by reducing the attack surface through its minimal device model, thereby improving resistance against potential cyber threats. By being developed in Rust, it guarantees thread and memory safety, preventing buffer overflows and other memory safety errors that can lead to security vulnerabilities. Firecracker ensures built-in security with compute security barriers for multitenant workloads that cannot be mistakenly turned off by customers, thereby protecting customer workloads and defending against any malicious activity.
Gen AI and Security at AWS: An interesting observation about Gen AI and Security is the CrowdStrike partnership with AWS, collaborating to develop advanced generative AI applications for cybersecurity, cloud, and AI use cases. CrowdStrike is leveraging the generative AI capabilities of Amazon Bedrock to enhance its Falcon Platform with improved search, reporting, and automation features, including the development of Charlotte AI, a generative AI security analyst. Using AWS services, CrowdStrike ensures the prevention, identification, and remediation of security risks associated with AI adoption.
Summary
The AWS re:Inforce conference announced significant advancements in cloud security and development acceleration, underscoring AWS’s commitment to enabling digital transformation and innovation for its customers. New services include Code Scans for Lambda function in Amazon Inspector, enhancing its automated security assessment capabilities; Amazon CodeGuru Security, a machine learning-based static application security testing (SAST) tool, guiding users on code vulnerabilities; and Amazon Verified Permissions, centralizing fine-grained permission policies using the open-source language Cedar. Partnerships with Deloitte, IBM Security, and Lacework were highlighted, offering improved security solutions and collaborations. AWS’s security strategy was illustrated through the AWS Nitro System, Firecracker software layer, and generative AI applications in partnership with CrowdStrike. These efforts combine to provide robust cloud security on AWS, fostering faster and safer application development.
